


Showing what can happen and why it's easy. One person was the victim of the
Back Orifice software program which allows the hacker to remotely view and
control any computer running Windows 95 or later. The hacker used Back Orifice
to observe what web sites the victim was visiting. Mari Frank was another
hacking victim--this time it was "identity theft." Her personal files on her
computer were accessed and a woman assumed Frank's identity and rang up over
$50,000 in credit card debt.
 |  | 
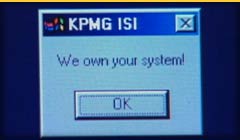

Sensational hacker attacks on large e-commerce and corporate sites get a lot
of media attention. But computer security analysts discuss in this videoclip
why these break-ins are probably only the tip of the iceberg and corporate
America is turning to their own private intelligence expencies to protect itself.
 |